Why it isn’t the act of falling but, rather, how your organisation picks itself back up that really matters.
In the digital era, a cybersecurity breach is as inevitable as death or taxes.
Most organisations will lament the latter, but when it comes to the former? Malware, Phishing Scams, and Zero-Day Exploits remain largely unfamiliar territory. Despite this inexperience, 76% of New Zealand organisations surveyed consider themselves well-prepared to deal with a cybersecurity attack:
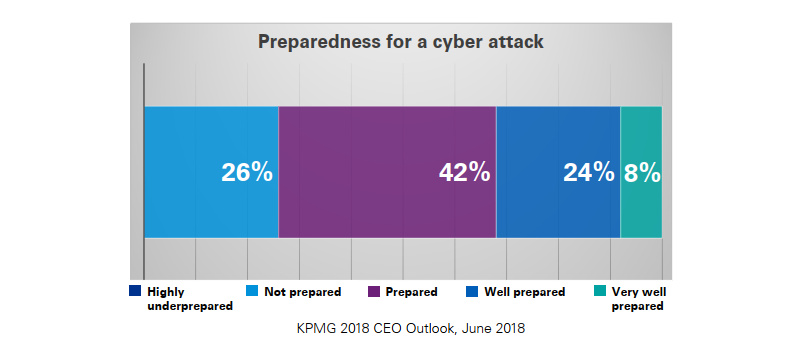
These figures should be uplifting, but in reality they’re anything but. Why? Because in the same survey it was found that the average cyber incident response maturity of New Zealand organisations sits at just 1.7, hovering somewhere between Initial and Ad-Hoc on a 5 point scale.
This discrepancy between perception and reality is putting organisations – and information – at risk.
Security breaches are a “When”, not “If”

As we’ve covered in the past, your organisation’s access to a wealth of highly sensitive, valuable information including intellectual property, sales data, and client documents – among others – makes it the prime target for a cyberattack.
Yet as these numbers show, very few – if any – organisations, enterprises, or even small to medium sized businesses are as prepared as they think they are when it comes to responding to an event like this.
That’s if they rate it at all. Look a little further abroad and you’ll find studies like the one conducted by Keeper which found that just 9% of businesses rank cybersecurity as a top business priority, while 60% say they do not have a cyberattack prevention plan in place.
This haphazard approach only exacerbates the effects of an inevitable cyber breach.
Recovery isn’t always guaranteed
Let’s take a moment to put the potential ramifications of these stats into context.
In 2015, Commissioner Luis A. Aguilar of the U.S. Securities and Exchange Commission did just this as he highlighted the need for greater attention on the cybersecurity challenges facing small and midsize businesses in an article for Cyber Security Review:
“It has been estimated that half of the small businesses that suffer a cyberattack go out of business within six months as a result.”
The stats, facts, and figures have only gotten worse since then:
Did you know?
These figures make it clear that an incident like this isn’t just costly, it can prove fatal. So while prevention may be better than a cure, preparing for the inevitable should still be a top priority for those looking to take cybersecurity seriously.
6 Steps that will help your board recover from a cybersecurity breach, with class

Convincing those at the top that cybersecurity needs to be taken seriously remains a big hurdle.
Yet even for those that do, an effective risk management plan and data security strategy cannot be considered ‘comprehensive’ if it doesn’t acknowledge the inevitability of a potential breach. Otherwise you’ll be left scratching your head with a plan that deals solely with prevention rather than recovery.
It’s easy to see why some may be apprehensive about adopting this kind of strategy. Some may interpret it as an admission of failure. In reality, being ready to act eliminates any delay in response, minimises downtime, limits bad press, and highlights that you’re aware of the realities of doing business in an increasingly connected world.
To help you along the way, here are a few suggestions for the hours, days, and weeks that follow:
1. Identify the breach
Many of today’s leading hacks, attacks, and breaches rely on their ability to remain hidden, where they slowly syphon important data as well as intercept emails and other network communications. It’s one of the major reasons we recommend you steer clear of hitting ‘Send’ on that next email.
Identifying these issues is a major hurdle on the road to recovery, but robust internal monitoring, tools, and systems should turn up any unusual traffic, unauthorised IP addresses, or mass login attempts, for example, ensuring they’re caught at the earliest possible time.
2. Set up virtual containment lines
Isolating the breach as well as any affected files or hardware minimises the damage and fast tracks recovery. Depending on the nature of the attack, this could include taking servers or systems offline, revoking access privileges, and updating credentials.
Limited oversight and control over who has access to what can make this task difficult, which is why it’s recommended that boards employ an effective business platform with a robust set of security features that make it easy to update or revoke access privileges for devices and data with the touch of a button.
3. Find the gap in the fence
Tasking relevant departments with identifying the weak links in the security fence is where real change is affected. The ultimate aim here is to leave your organisation in a stronger position that it started.
It isn’t uncommon to face internal pressure at this time to fast track the process, and return to business as usual at the earliest possible date. However, effective recovery cannot be rushed. Unless these flaws are addressed, your organisation is simply inviting repeat attacks.
4. Survey the damage
Upon triaging these digital wounds, it’s time to take stock and ascertain the severity of the breach. Was customer or employee data accessed? Copied? Stolen? What about sensitive information, data, or intellectual property?
Looking at it from this point of view, you’ll be able to identify whether this was simply the work of ‘Hacktivist’ hobbyist groups, or a legitimate attempt to siphon valuable data from your business.
Internal departments should be able to quickly and easily audit all internal files, folders, and other data for suspicious activity. More importantly, any affected files can then be restored from Cloud backups or replicas, as outlined in your disaster recovery plan.
5. Notify those affected
In the aftermath of many of the 21st century’s largest security breaches, the silence has been deafening. Many corporations embrace a softly softly approach, which sees them talking in circles and spinning PR until the truth inevitably surfaces. In this context, recovery becomes that much more difficult.
The truth of the matter is that yes, you’re likely to face bad press post-security breach. However the long-lasting impact of a lack of transparency with press, customers, or clients, can further place your name in poor standing.
As far as is reasonable according to internal policies and law, honesty is always the best policy.
Many countries actually enact harsh consequences for non-disclosure. Under the General Data Protection Regulation (GDPR), for example, you are required to “…report certain types of personal data breach to the relevant supervisory authority. You must do this within 72 hours of becoming aware of the breach, where feasible.“
An open, honest recovery is the only path to rebuilding trust in the court of public opinion. For most customers or clients, the next best thing to an organisation that’s free of issues is one that is aware of – and proactively working to solve – them when they arise.
6. Prepare for the next one
At the time it will be difficult for your organisation to see a data breach as anything other than a hassle, but it’s also a learning opportunity if approached in the right manner. Theoretical planning will only get you so far, but being able to work through – and recover from – a real-world security breach enables you to identify gaps in policies, procedures, and IT infrastructure.
More importantly, you can look back over how the breach was handled, how it was received, and further modify your response so that you can minimise downtime, close vulnerabilities, and keep clients better informed when – not if – there is a next time.
Further secure your files with the right business platform
Keeping information secure and out of reach of cyber attackers, hackers, and other third parties can prove difficult in this day and age, as can salvaging lost files, data, or sensitive information in the wake of a breach.
That’s why we’ve always been proponents of a secure business platform that is able to all at once robust enough to mitigate against a breach as well as reliable enough to make the recovery process as smooth and seamless as possible.
Sticking the landing and saving face may be difficult, but it doesn’t have to be impossible. With the right solution boasting multi-level security protocols and industry-leading encryption you’ll be able to securely store, share, and send files while being better situated than ever to recover from a breach with your files, data, and reputation intact.
